
Integration between Ongoing WMS and Microsoft Entra ID
Table of contents
Introduction
Microsoft Entra ID (formerly Microsoft Azure AD) is an identity provider, that is, a service which allows you to keep all information about your users in centralized location. Ongoing WMS has an integration with Entra ID which features Single Sign-On (SSO) and User Provisioning. For general information about identity providers in Ongoing WMS, please see Connect an identity provider (IdP) to Ongoing WMS.Configuration
Ongoing WMS does not have a registered application in the Microsoft Entra Gallery. Therefore you must create a new app registration in your Entra tenant. This will also create a service principal (also known as Enterprise Application) that Ongoing WMS uses to authenticate against your tenant to retrieve the necessary information for SSO. The same application can be used to provide both Single Sign-On and User Provisioning.
- Go to Microsoft Entra admin center ⇒ Entra ID ⇒ Enterprise applications.
- Click New application.
- Click Create your own application.
- Name it "Ongoing WMS" or similar, and ensure Integrate any other application you don't find in the gallery is marked.
- Click Create.
Single sign-on (SSO)
This section provides instructions on how to configure Microsoft Entra ID for SSO in Ongoing WMS. It assumes that an application has already been created in Entra, see above instructions. Note that Microsoft has similar documentation but with more details, see Microsoft Learn: Enable SAML single sign-on for an enterprise application to learn more.
-
Start by creating an IdP configuration in Ongoing WMS (if one has not been created already). In Ongoing WMS, go to Administration ⇒ Identity providers.
- To create a new IdP configuration, Click Create new identity provider.
- To edit an existing IdP configuration, click the pen-icon on the row.
- Check Enable SSO
- In Entra, navigate to Enterprise applications ⇒ Ongoing WMS ⇒ Single sign-on.
- Choose single sign-on method SAML.
-
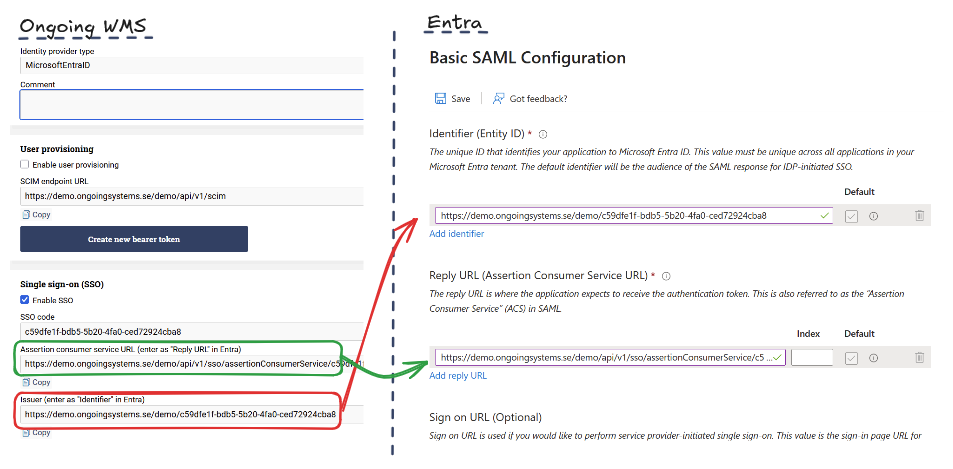
Edit Basic SAML Configuration:
- From Ongoing WMS, copy Assertion consumer service URL to Reply URL in Entra.
- From Ongoing WMS, copy Issuer to Identifier in Entra.
-
In Entra, click Save.
-
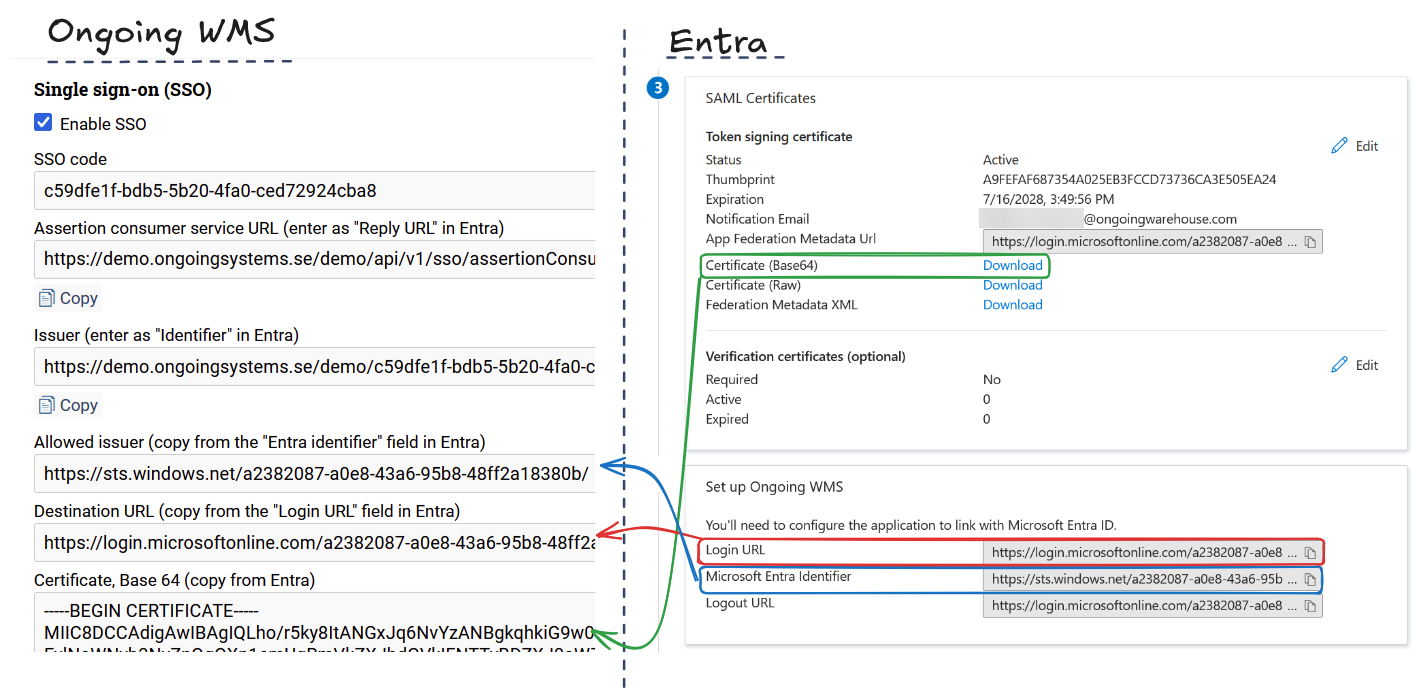
The remaining information is to be copied from Entra to Ongoing WMS and is found in SAML Certificates and Set up Ongoing WMS in Entra:
- From Entra, copy Microsoft Entra Identifier to Allowed issuer in Ongoing WMS.
- From Entra, copy Login URL to Destination URL.
-
From Entra download Certificate (Base64) and copy to Certificate in Ongoing WMS.
- Click Create or Update in Ongoing WMS to save the information.
In Entra, navigate to Ongoing WMS Enterprise Application ⇒ Properties. If you have Assignment required set to Yes (default), then you must also scope which users and/or groups that will be able to use SSO. Refer to Microsoft Learn: Manage users and groups assignment to an application on how this is done.
Now you should be able to test SSO:
- Ensure there exists a user in Ongoing WMS with a username that matches a user's User Principal Name (UPN) in Entra.
- Log out from Ongoing WMS.
- Press the new button that has appeared - Log in via single sign-on (SSO).
- Complete the Entra login sequence.
User provisioning
This section provides instructions on how to configure user provisioning from Microsoft Entra ID to Ongoing WMS. It assumes that an application has already been created in Entra, see above instructions.
-
Start by creating an IdP configuration in Ongoing WMS (if one has not been created already). In Ongoing WMS, go to Administration ⇒ Identity providers.
- To create a new IdP configuration, Click Create new identity provider.
- To edit an IdP configuration, click the pen-icon on the existing row.
- Check Enable user provisioning.
- In Entra, navigate to Enterprise applications ⇒ Ongoing WMS ⇒ Provisioning.
- Follow the instructions in Entra for setting up provisioning, or see the documentation Microsoft Learn: Managing user account provisioning for enterprise apps in the Microsoft Entra admin center.
-
The following information has to be transferred from Ongoing WMS to Entra ID:
- SCIM endpoint URL to Tenant URL.
- Bearer token to Secret Token.