Security for users in the WMS
Table of contents
Introduction
It is vital that no unauthorized persons get access to Ongoing WMS. In the following sections we will go through some precautions you as an administrator to Ongoing WMS can take, to make sure that no unauthorized persons get access to your instance of Ongoing WMS. To learn more about how Ongoing as a company work with IT security, please visit our Trust Center.
Best practices
The following are regarded as best practices for users:
- Consider integrating with an identity provider (IdP) such as Microsoft Entra ID (formerly Microsoft Azure AD). This will allow you to use single sign-on (SSO), so that each a user can be authenticated by Entra rather than by Ongoing WMS.
- Consider turning on two-factor authentication (2FA).
- Consider configuring more complex password requirements.
- Consider locking certain accounts to specific IP ranges.
- Do not allow users to share accounts. If you have temporary workers in your warehouse, make sure that they all have their own accounts.
- Users should have the minimal permission level required for them to carry out their work. Do not make users Administrators if they can carry out their work as a Warehouse Worker.
- Only allow users to access the goods owners that are necessary for them to carry out their work.
- Configure the system to automatically inactivate users which have not been used for a long time.
- Regularly review your users and remove those that are no longer necessary. This can be done once a month.
- Consider restricting access to the users administration page.
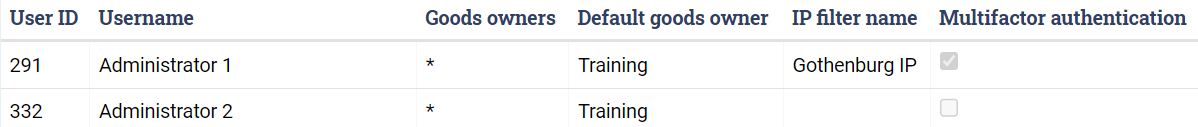
In Administration ⇒ Users, you can easily see which users have two-factor authentication and IP filters turned on. The below picture shows two users. The first user has both two-factor authentication and an IP filter, while the second user has neither:
Password complexity requirements
Under the page Administration ⇒ Users you can configure password complexity requirements by navigating to the page settings. It is possible to adjust the minimum number of characters, minimum number of digits, minimum number of upper-case characters and minimum number of lower case characters. You can never configure anything less complex than 8 characters, 1 lower case character, 1 upper-case character and 1 digit.
It is not possible to reuse passwords. That is to say: When a password is changed, it has to be changed to a new password. It is not possible to use an old password again.
Two-factor authentication / Multi-factor authentication
By default, a user may log in to Ongoing WMS if they know their username and password. You can increase security by turning on two-factor authentication (2FA). When 2FA is turned on, the user must provide an additional factor (a PIN code) every 30 days.
2FA is also known as multi-factor authentication (MFA).
Note that if you log in using single sign-on (SSO), then you will bypass any 2FA which has been set up in Ongoing WMS.
The PIN code can either be delivered to the user via e-mail, or by an authenticator app on the user's smartphone. Both Microsoft and Google provide authenticator apps. We support most authenticator apps.
From the user's perspective, it works like this:
- The user attempts to login with their username and password.
-
A PIN code is delivered to the user. Depending on how you have configured 2FA for the user, either:
- The PIN code gets sent to the user's email address, or
- The user opens an authenticator app on their smartphone (such as Google Authenticator or Microsoft Authenticator) and gets a PIN code from the app.
- The user is asked to input the PIN code, which they must do before they are allowed to login.
- If the user tries to login again from the same machine within 30 days, they will not be asked for a PIN code. After 30 days, they will be asked for a PIN code again.
In most cases, a user can turn on 2FA themselves by going to the page "System ⇒ Two-factor authentication". If that page is not available for the user, the administrator has to turn on 2FA for the user:
- Go to Administration ⇒ Users.
- Click on "Manage two-factor authentication".
- Locate the setting called "Two-factor authentication via email" or "Two-factor authentication via an authenticator app".
- Click on the Edit icon and select the users who should have 2FA activated.
- In the case of 2FA via an authenticator app, the next time the user logs in, they will be asked to add the account to their authenticator app.
We have written a guide intended for users on how they can turn on 2FA on their account.
Resetting a user's authenticator app
If a user has been set up with two-factor authentication via an authenticator app, then they must have access to the app to login to Ongoing WMS. This means that if the user loses their phone or if their phone breaks, they will not be able to login to Ongoing WMS.
If that happens, the administrator of Ongoing WMS will have to reset the user's 2FA setting:
- Go to Administration ⇒ Users.
- Find the user and click on Edit.
- Click on "Reset the user's two-factor authentication key".
Not requiring 2FA from certain IP ranges
The system can be set up so that two-factor authentication (2FA) is not required when logging in from certain IP ranges. So if your warehouse has fixed IPs, you can set it up so that 2FA is required when logging in from outside the warehouse, but not when logging in from inside the warehouse.
To set it up:
- Go to Administration ⇒ Users.
- Click on "Manage IP filters".
- Create a new IP filter and make a note of its ID.
- Go back to Administration ⇒ Users.
- Click on "Manage two-factor authentication".
- Click on the Edit icon for the correct setting.
Then click on the setting in the list to the right. Then click Edit, enter the IDs of the IP filters, then click Update:
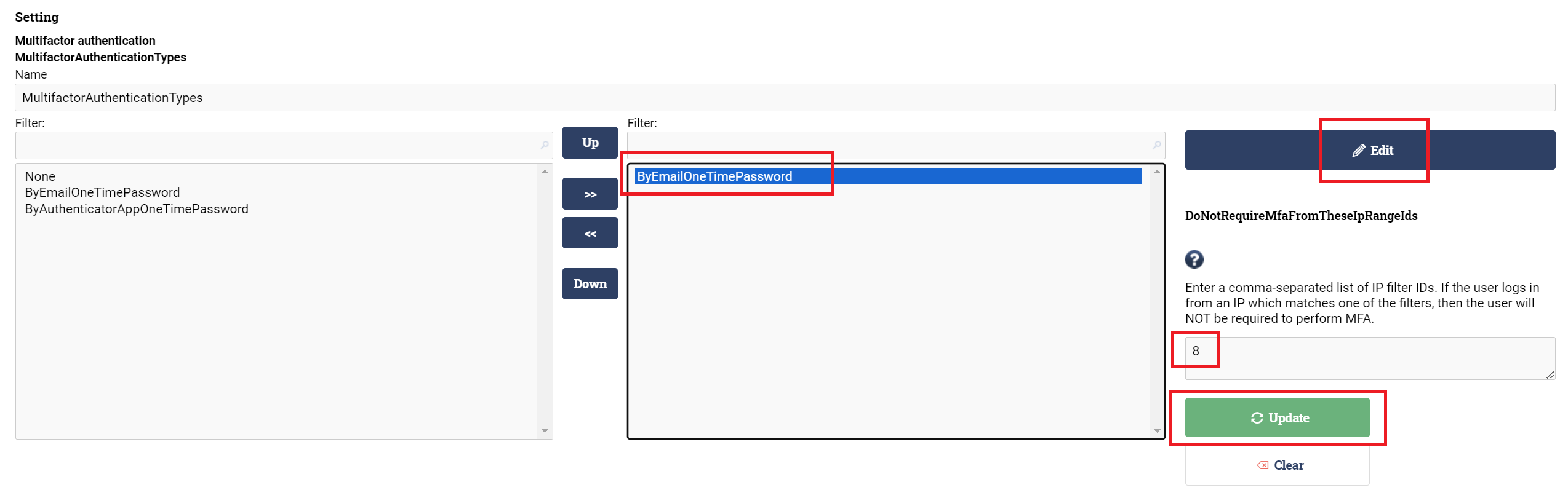
Finish by clicking on the Update button at the bottom:

Requiring a user to register for 2FA
By default, a user is allowed to postpone registering for 2FA indefinitely. This can be changed so that the user must register for 2FA before they are allowed to do anything else.
To apply this setting:
- Go to Administration ⇒ Users.
- Click on "Manage two-factor authentication".
- Find and edit the setting which applies for the user in question.
- In "disallow postpone after this date", enter tomorrow's date. (For technical reasons, we do not recommend putting today's date here since it may interrupt the user's current work.)
This means that if the user logs in after "tomorrow", then they have to register for 2FA.
IP filters
By default, a user may log in to Ongoing WMS from any IP address. You can increase security by only allowing certain users to login from specific IP ranges. For instance, if your warehouse has a specific IP range then you can restrict all of your Warehouse Worker users so that they can only login from that IP range, thus restricting outside access.
Note that if you log in using single sign-on (SSO), then you will bypass any IP filters which have been set up in Ongoing WMS.
There are two steps to setting this up. The first step is to define one or more IP filters:
- Go to Administration ⇒ Users.
- Click on "Manage IP filters".
- Click on "Create new IP filter".
- Enter a description of the IP filter (e.g. "IP addresses for my warehouse").
- Enter which IP ranges should be allowed in the filter. Each IP range is described using the standard subnet notation like "217.28.199.21/32". An IP filter can contain several IP ranges.
- Click on "Create".
The second step is to update the users:
- Go to Administration ⇒ Users.
- Find a user.
- Click on the Edit icon.
- Select the IP filter which you want the user to have.
- Click on "Update".
- Repeat for all users. You can also use the "Multiple update" to update several users at the same time.
When specifying an IP filter, you should usually specify an actual IP range such as "217.28.199.21/32". However, it is allowed to specify a domain (e.g. "subdomain.yourdomain.com") if you want a dynamic IP filter. In that case, make sure that the TTL on the subdomain is very short to prevent caching issues.
Restrict access to the user administration page
By default, all administrators have access to the user administration page. Consider restricting access to this page so that only a few administrators can access it. Send the list of administrators to your contact person at Ongoing, and they will make the necessary adjustments.
Automatically inactivate users which are unused
By default, Ongoing WMS does not inactivate users which are unused. There is a configuration setting which controls which users are automatically inactivated if they have been unused for too long.
Go to Administration ⇒ Users and click on the settings icon (the cog wheel) at the bottom of the page. Create a new setting for "Inactivate unused users", or edit the existing setting if one exists.
The setting allows you to choose how many days Ongoing WMS should wait before inactivating an unused user, and also which user types should be considered. For instance, you can set it up so that Administrators and Warehouse Workers are inactivated after 60 days of not having been used.
If you need to re-activate a user, simply go to Administration ⇒ Users, find the user in the table, and click on the Edit icon. Then check the "User is activated" checkbox and save the user.